Rumble Cloud Guide to IP Addresses¶
Rumble Cloud is powered by modern OpenStack technology and offers flexible options for IP address management within customer-owned virtual networks (VPCs) and subnets.
In this guide:
- Outlines how IP addresses can be assigned and used
- Answers common questions around dynamic and static addressing within virtual machines (VMs)
- Explains some more advanced network capabilities
IP address allocation¶
Allocation methods¶
When creating ports or launching VMs within your Rumble Cloud project, you have two options for assigning IP addresses:
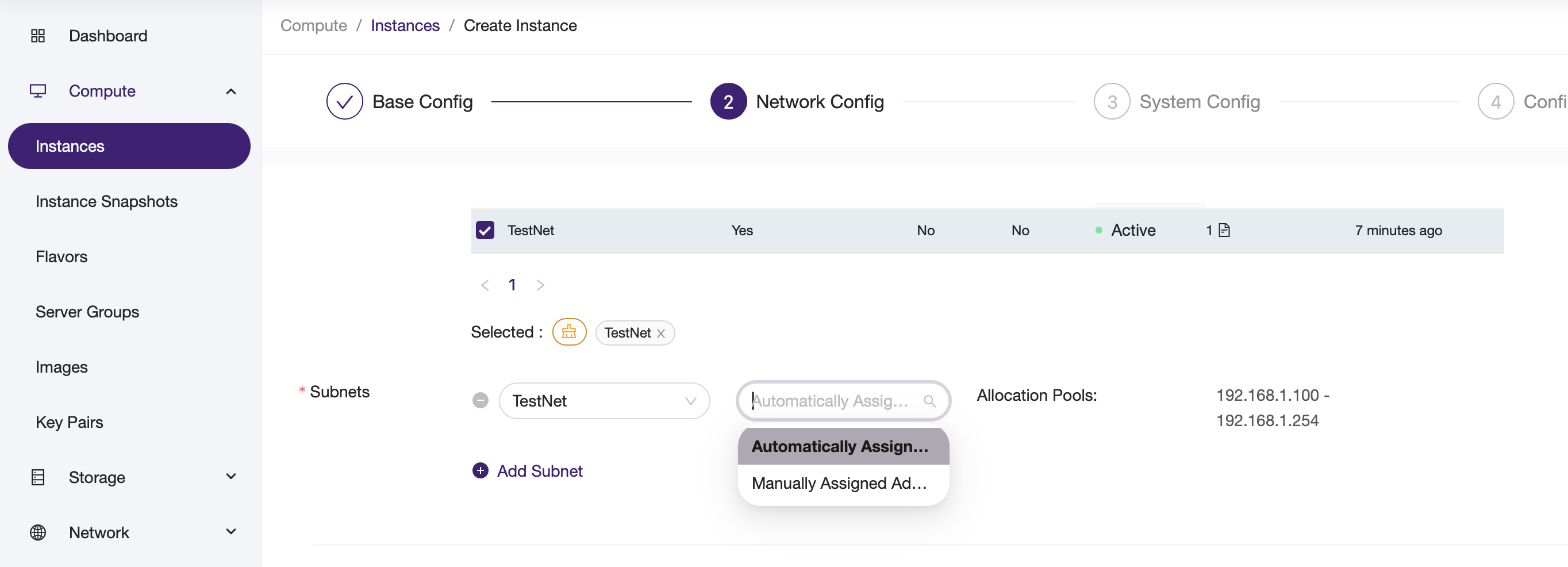
1. System-allocated IP¶
- Rumble Cloud automatically assigns an IP address from the subnet’s defined allocation pool.
- The assigned IP is guaranteed not to conflict with other active IPs in the subnet.
Cloud Console¶
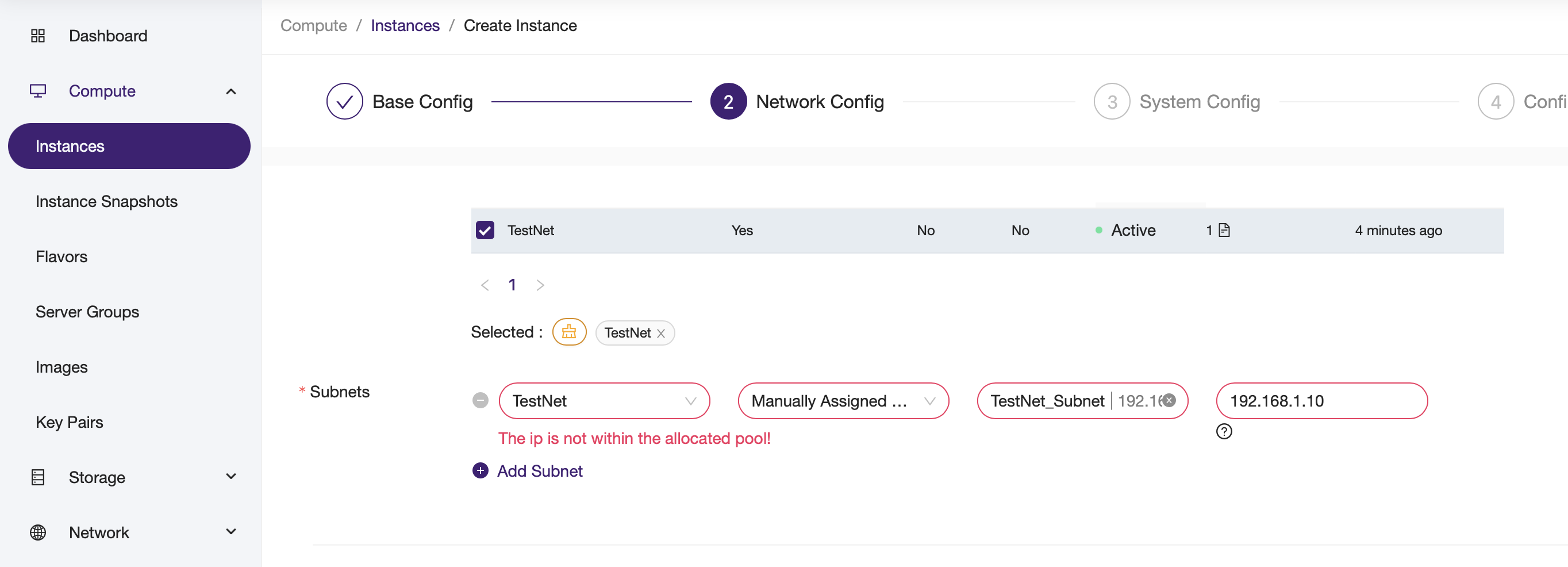
2. Manually assigned IP¶
- You can manually specify an IP address when creating a port or attaching a network to a VM.
- The IP can be inside or outside the subnet’s allocation pool.
- Note the web interface may show a warning if the IP address is outside of the allocation pool, but this is only a warning. It is safe to use an IP outside of the allocation pool as long as its not already used.
Cloud console¶
DHCP vs static IP inside the VM¶
The method used within the VM to configure the IP address is independent of how the IP was allocated in Rumble Cloud.
| IP Allocation Method | DHCP Inside VM | Static IP Inside VM |
|---|---|---|
| System-Allocated | Yes — IP is delivered via DHCP | Yes — You can manually assign the same IP inside the VM |
| Manually Assigned | Yes — If DHCP is enabled, the IP will be served | Yes — You can configure the IP manually in the guest |
- If DHCP is enabled on the subnet, any assigned IP (manual or system) can be delivered automatically to the VM via DHCP.
- If DHCP is not used, the VM must be configured manually (or via some other automation methodology) to match the assigned IP.
Important notes¶
- Rumble Cloud tracks and manages IP-to-port mappings regardless of DHCP/static configuration inside the guest.
- Manually assigning an IP to a VM’s interface does not bypass Rumble Cloud’s network security or routing controls.
- You can safely use static IPs even with system-assigned addresses, as long as you match the IP seen in the port metadata.
- Even when manually assigning an IP, Rumble Cloud will not allow address conflicts when using standard IP port address assignment. However, if you utilize advanced features by assigning "Allowed Address Pairs" or disabling port security (see below for details), then address conflicts are possible. Address conflicts are your responsibility if using these advanced capabilities.
Using allowed address pairs to provide advanced functionality such as VIP's¶
The Allowed Address Pairs feature lets you associate additional MAC/IP address combinations with a network port. This enables traffic to be accepted from IP addresses not originally assigned to the port. This is useful for advanced networking scenarios.
What are allowed address pairs?¶
By default, ports are strict: a virtual machine (VM) is only allowed to send and receive traffic using its assigned fixed IP and MAC address. If a VM sends traffic using an unexpected IP, it will be dropped by the virtual switch for security.
Allowed Address Pairs relax this restriction by letting you explicitly declare additional (MAC, IP) pairs that are permitted on the port.
Common use cases¶
- Virtual IPs for High Availability (e.g., using Keepalived or Pacemaker)
- Load Balancers (e.g., HAProxy or Octavia active-standby)
- Floating IP forwarding for NAT gateways or routers
- Multi-IP interfaces for custom apps
How it works¶
Each port can be configured with one or more allowed address pairs via the CLI or API. They cannot currently be configured via the web interface.
Example: Add a virtual IP to a port¶
This allows the VM using my-port-id to send traffic from 192.168.1.100, in addition to its regular fixed IP.
You can also specify a different MAC if needed:
openstack port set \
--allowed-address ip-address=192.168.1.100,mac-address=fa:16:3e:12:34:56 \
my-port-id
Important notes¶
- Allowed address pairs can ONLY be used on internal project networks owned by your project. For security reasons, they can not be used on public or external networks.
- Security groups still apply. You must ensure your security groups allow traffic to/from the allowed IP.
- The MAC address defaults to the port’s MAC if not specified.
- Be cautious when adding wildcard entries (e.g.,
ip-address=0.0.0.0/0) they can easily result in ip address conflicts and other complications. - Useful in conjunction with HA failover services where the virtual IP moves between VMs.
Verifying allowed address pairs¶
To see current allowed address pairs on a port:
Or with YAML output:
¶
Security implications¶
- Use least privilege: only add address pairs that are truly needed.
- Consider disabling port security entirely for NAT/routing VMs where forwarding is required — but understand the risks.
Disabling port security in OpenStack¶
Another option for advanced networking is to disable port security on your VM ports. By default, Rumble Cloud enables port security to prevent IP spoofing, and control MAC address usage on virtual interfaces. However, there are certain use cases where you need more control, and therefore disabling port security is necessary and appropriate.
What Is port security?¶
Port security enforces the following rules by default:
- A VM can only use its assigned IP address(es).
- A VM can only use its assigned MAC address.
- Security group rules apply to all traffic to/from the port.
These protections are critical for cloud environments to prevent:
- IP/MAC spoofing
- Unauthorized traffic forwarding
- Unrestricted L2/L3 behavior
Since this behavior could be malicious if performed on a public network, disabling port security is only possible on internal project networks in Rumble Cloud.
What happens when you disable port security?¶
Disabling port security on a port removes the restrictions on:
- Source IP and MAC address enforcement
- Security group enforcement (no firewalling)
This allows the instance to:
- Forward packets from other IPs (e.g., NAT, routing)
- Receive traffic from arbitrary sources
- Act as a router, load balancer, or bridge
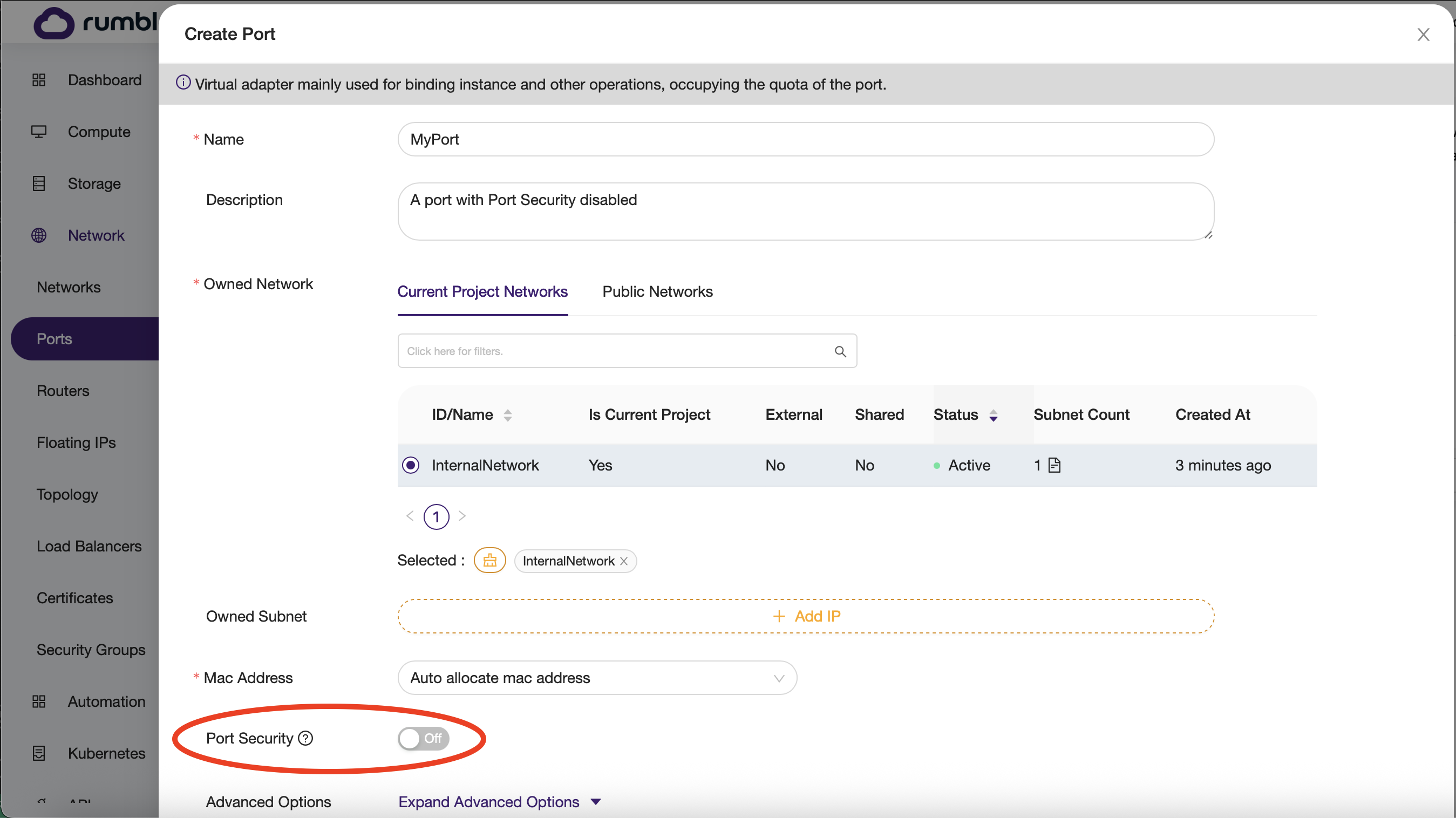
How to disable port security¶
When creating a port:¶
CLI¶
openstack port create \
--network my-network \
--no-security-group \
--disable-port-security \
my-port
Cloud console¶
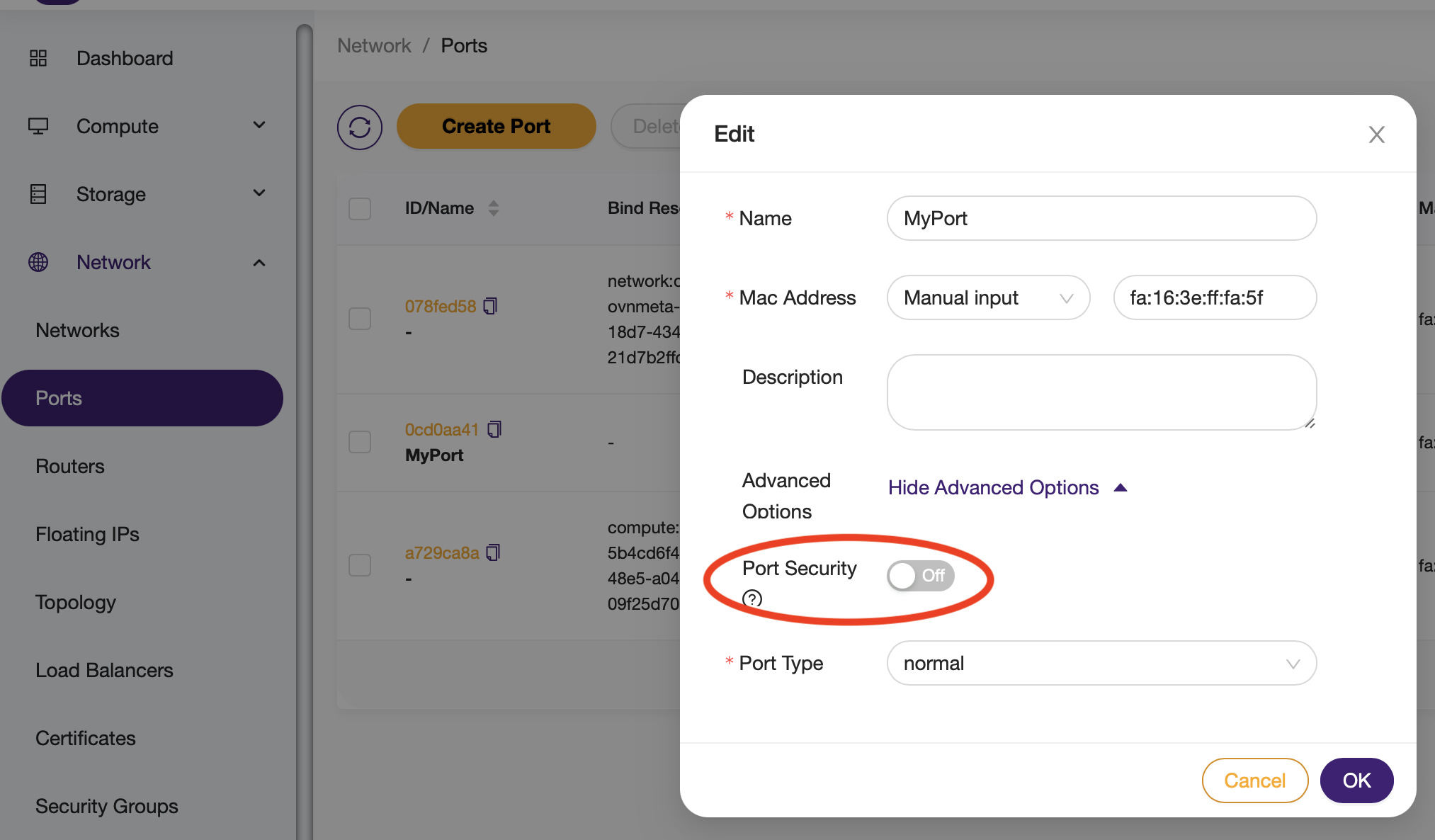
On an existing port:¶
CLI¶
Cloud console¶
When should you disable it?¶
Disabling port security is required or recommended in scenarios like:
- Virtual routers (e.g., using Linux
iptablesornftables) - NAT gateways
- Load balancer VMs forwarding traffic
- Custom L2/L3 appliances (firewalls, VPNs, etc.)
Important notes¶
Disabling port security gives a VM full freedom to:
- Spoof MAC/IP addresses
- Send/receive any traffic
- Interfere with other tenant networks (if improperly isolated)
Never disable port security unless:
- The VM's behavior is well understood
- You’ve implemented external controls (e.g., ACLs, router filters)
For additional information about advanced networking scenarios or troubleshooting help, contact Rumble Cloud Support.